This guide is written by myself so that I do not forgot how to do this again in the future. This should remind me how to set up DNSSEC with BIND 9.9 complete with keys rollover scheme that should be painless to implement.
I assume that you already have:-
- BIND 9.9 installed. Older version doesn’t work with this guide. And trust me, you don’t want to deal with dynamic zones which DNSSEC-enabled BIND <9.9 have created unless you have to. This guide used CentOS 6, therefore the process is called ‘named’, running under the user ‘named’, using the daemon called ‘named’.
- Fully working .my zone(s) in that BIND installation.
- Technical contact access in domainregistry.my control panel for your .my domain.
First, ensure that DNSSEC is enabled in the BIND install (it should be on by default).
options {
listen-on port 53 { 127.0.0.1; };
listen-on-v6 port 53 { ::1; };
directory “/var/named”;
dump-file “/var/named/data/cache_dump.db”;
statistics-file “/var/named/data/named_stats.txt”;
memstatistics-file “/var/named/data/named_mem_stats.txt”;
recursion no;
version “It’s over 9000”;dnssec-enable yes;
dnssec-validation yes;
dnssec-lookaside auto;
sig-validity-interval 30 8;/* Path to ISC DLV key */
bindkeys-file “/etc/named.iscdlv.key”;managed-keys-directory “/var/named/dynamic”;
};
Because DNSSEC with key rollovers produced plenty of keys, each zone should have their own keys directory! In “/var/named” folder, create a folder intuitively titled ‘keys’. Then in that ‘key’s folder, create in it a folder for your domain name’s keys. Lets titled it anime.my for example (I own this domain). Therefore, the keys will be ultimately located in ‘/var/named/keys/anime.my’ folder.
You need of course to tell named.conf about the keys’ location in the zone option, using the ‘key-directory’ option. Also put the ‘inline-signing yes’ and ‘auto-dnssec maintain’ options in the zone option.
zone “anime.my” {
type master;
file “anime.my.conf”;
key-directory “keys/anime.my/”;
inline-signing yes;
auto-dnssec maintain;
};
Make your way to the ‘/var/named/keys/anime.my’ directory. The first step to do is to create a key signing key (KSK) for the domain. In the shell, type:-
dnssec-keygen -f KSK -a RSASHA512 -b 1024 -n ZONE -I <yyyymmdd> -D <yyyymmdd> anime.my
Two files will be created in the ‘/var/named/keys/anime.my’ directory, for example, something like ‘Kanime.my.+010+12345.key’ and ‘Kanime.my.+010+12345.private’ files. Please take note so that you remember that the ‘Kanime.my.+010+12345.*’ is your KSK keys.
Because this key is a key signing key file, the date in -I <yyyymmdd> should be quite distant in the future, should be at least a year or so from the time of signing. Therefore, if you are reading this in January 2012 for example, set the -I argument to the end of the 2012 year for example. Of course, this is all to your discretion. I’ll use the end of 2013 for example below.
The date in the -D <yyyymmdd> should be 7 to 14 days after the date you specify in the -I <yyyymmdd> arguement. Simple as that.
A fully working example of a KSK file being generated so that it become inactivated at the end of 2013, and then deleted 14 days later, should look like below:-
dnssec-keygen -f KSK -a RSASHA512 -b 1024 -n ZONE -I 20131231 -D 20140114 anime.my
Now we move on to creating a zone signing key (ZSK) for the domain. In the shell, type:-
dnssec-keygen -a RSASHA256 -b 512 -n ZONE -I <yyyymmdd> -D <yyyymmdd> anime.my
Two files will be created in the ‘/var/named/keys/anime.my’ directory, for example, something like ‘Kanime.my.+008+67890.key’ and ‘Kanime.my.+008+67890.private’ files. Please take note so that you remember that the ‘Kanime.my.+008+67890.*’ is your ZSK keys.
Because this key is your zone signing key, the date in the -I <yyyymmdd> argeument should be at most 3 or 4 months from creation. Therefore, if you are reading this in January 2012 for example, set the -I arguement at the end of March 2012 for example. This is not at your discretion, the date chosen really cannot be too long than 3 or 4 months from the date of creation, but should be longer than 30 days. I’ll use the end of November 2012 for example below.
The date in the -D <yyyymmdd> should be 7 to 14 days after the date you specify in the -I <yyyymmdd> arguement. Simple as that.
A fully working example of a ZSK file being generated so that will be inactivated at the end of November 2012, and then deleted 14 days later should look like below:-
dnssec-keygen -a RSASHA256 -b 512 -n ZONE -I 20121130 -D 20121214 anime.my
Now, we are going to set up one successor key for the KSK file that BIND will automatically put into place when the first KSK file expired. From the above, the example KSK file is the ‘Kanime.my.+010+12345.*’ combo and this file will expire at the end of 2013. In the shell, type:-
dnssec-keygen -S Kanime.my.+010+12345.key -I <yyyymmdd> -D <yyyymmdd> -i 60d
The date in the -I arguement should be at least one year from the expiration of the first KSK file (the Kanime.my.+010+12345.key which will happen at the end of 2013). The date for the -D argument is 7 to 14 days after the date you choose for the successor key’s -I arguement. A fully working example of a successor KSK file that will expire at the end of 2014, and deleted 14 days later is:-
dnssec-keygen -S Kanime.my.+010+12345.key -I 20141231 -D 20150114 -i 60d
A new pair of KSK files, for example, something like ‘Kanime.my.+010+54321.key’ and ‘Kanime.my.+010+54321.private’ will be created. Take note so that you remember that this pair of KSK file is the successor for the ‘Kanime.my.+010+12345.key’ and ‘Kanime.my.+010+12345.private’ files. If the expiry of the sucessor KSK file nears, just run the dnssec-keygen command again with the -S arguement against the successor key, to create yet another successor key for key rollover.
Now we are going to set up 3 successor keys for the ZSK file that BIND will automatically put into place when the first ZSK expired. From above, the example ZSK file is the ‘Kanime.my.+008+67890.*’ combo and this file will expire at the end of November 2012. In the shell, type:-
dnssec-keygen -S Kanime.my.+008+67890.key -I <yyyymmdd> -D <yyyymmdd> -i 60d
The date in the -I arguement should be between 3 to 4 months from the expiration of the first ZSK file (the Kanime.my.+008+67890.key which will happen at the end of November 2012). The date for the -D argument is 7 to 14 days after the date you choose for the successor key’s -I arguement. A fully working example of a successor ZSK file that will expire three months after being activated to replace the first SZSK, and deleted 14 days later is:-
dnssec-keygen -S Kanime.my.+008+67890.key -I 20130228 -D 20130314 -i 60d
The first ZSK key replacement pair will be created, something like ‘Kanime.my.+008+09876.key’ and ‘Kanime.my.+008+09876.private’ for example. Please take note so that you remember that this is the first successor key to the original ZSK file. Now we are going to create the successor for this newly minted first ZSK key successor, with the same 3 months expiry time limit and deletion 14 days later. In the shell type:-
dnssec-keygen -S Kanime.my.+008+09876.key -I 20130531 -D 20130614 -i 60d
This will create the second pair of successor keys, something like ‘Kanime.my.+008+99799.key’ and ‘Kanime.my.+008+99799.private’ for example. Please take note so that you remember that this is the second successor ZSK file to the first successor ZSK file. Now we are going to create the successor for this newly minted second ZSK key successor, with the same 3 months expiry time limit and deletion 14 days later. In the shell type:-
dnssec-keygen -S Kanime.my.+008+99799.key -I 20130831 -D 20130914 -i 60d
This will create the third pair of successor keys, something like ‘Kanime.my.+008+99799.key’ and ‘Kanime.my.+008+99799.private’ for example. Please take note so that you remember that this is the third successor ZSK file to the second successor ZSK file. If the expiry of the successor ZSK file nears, just run the dnssec-keygen command again with the -S arguement against the third successor key, to create yet another successor key for key rollover. Repeat and rinse.
After all those keys creating binge, run this command in the shell:-
chown named:named *
Restart the bind daemon by running the ‘service named restart’), and within the same directory where the anime.my zone file (in this case, it’s called ‘anime.my.conf’) is located, 3 extra files will be created. They are:-
- anime.my.conf.jbk
- anime.my.conf.signed
- anime.my.conf.signed.jnl
in addition of anime.my.conf file. With this, the domain should already be signed.
Now log in into your domainregistry.my, with your technical contact credentials.
Go to ‘Domain Name —> DNSSEC —> Enable/Disable DNSSEC’. Then search for your domain name.
Then under the ‘DNSSEC status’, click the ‘Enable’ radio button and click the ‘Submit’ button. In the next page, click the ‘Confirm’ button.
Go to ‘Domain Name —> DNSSEC —> Update Key’, and search the domain whose DNSSEC has just been enabled. Tick the domain, and then click the ‘View Details’ button.
In the next page, which should look like something below:-
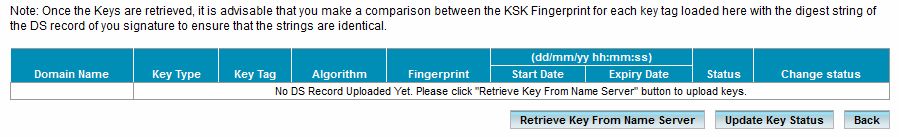
Click the ‘Retrieve Key From Name Server’ button, and it should be populated like what you see below.
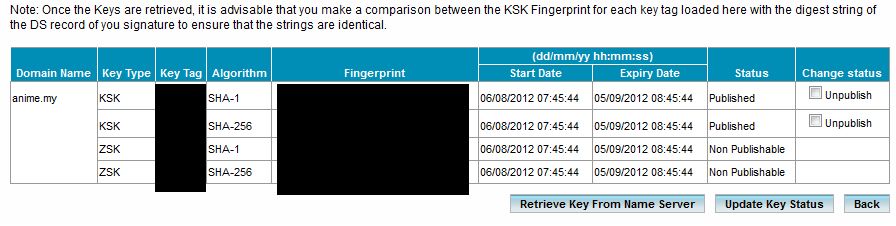
Wait for a few hours before the keys was published, and you will get yourself something like this. You do not have to do anything else at the domainregistry control panel, because it will download new key periodically before rollovers happens. Aff you have to do now is to ocassionally create successor keys for BIND and that’s it!
# dig anime.my +dnssec MX @unbound.odvr.dns-oarc.net
; <<>> DiG 9.9.1-P2-RedHat-9.9.1-P2.el6 <<>> +dnssec anime.my MX @unbound.odvr.dns-oarc.net
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 26941
;; flags: qr rd ra ad; QUERY: 1, ANSWER: 7, AUTHORITY: 6, ADDITIONAL: 1;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags: do; udp: 4096
;; QUESTION SECTION:
;anime.my. IN MX;; ANSWER SECTION:
anime.my. 7071 IN MX 30 aspmx3.googlemail.com.
anime.my. 7071 IN MX 10 aspmx.l.google.com.
anime.my. 7071 IN MX 20 alt1.aspmx.l.google.com.
anime.my. 7071 IN MX 20 alt2.aspmx.l.google.com.
anime.my. 7071 IN MX 30 aspmx2.googlemail.com.
anime.my. 7071 IN RRSIG MX 8 2 7200 20120830022534 20120809012534 34641 anime.my. p9YmBH0vCBte763KQhRz6HNA3kQVx+UKB3iydkviuef4jJs/vagkrMwL ADJs1+jczTvNGpGR6liy9ScTsuB2AQ==
anime.my. 7071 IN RRSIG MX 10 2 7200 20120830022534 20120809012534 18819 anime.my. bpOJdwNA6KZ3FoO0GLigTkz3sgMCN/1cyDpcO4DZnXfHNGybzVU8A/Vd /BRUT4R0m2skJH4ML7VwZ2P8FMiI4FxtGWKKsjgyNPPv316m5eGuVv2E f7B+tRFtyAYCxQoM9axOz4NlcL39kQKENJ9pIDMUO8IqoZxWnTTG8Tsy byJRvqE1ydu9iTBBNwhGUYjfdGrMSX9K0pmMwchvZG2vYeuTVxZ8DSjh 1jEqaZkmiGLx51egtW8YtqEW+BR/99euD7DkInduQDE5vhrMrGzbJ+F1 uEdNnz0R4+UVTvS/U9Pjotp7zZS86EOends3c9mViTyupV9nJ+3ZEXAd N7OKpQ==;; AUTHORITY SECTION:
anime.my. 7043 IN NS ns7.dnsmadeeasy.com.
anime.my. 7043 IN NS ns6.dnsmadeeasy.com.
anime.my. 7043 IN NS k1.ahmygoddess.net.
anime.my. 7043 IN NS ns5.dnsmadeeasy.com.
anime.my. 7043 IN RRSIG NS 8 2 7200 20120830022534 20120809012534 34641 anime.my. G00MWsOaAg3ld4jjNrBdvXrY6t+ev06GyIs0MoscANTLNbp3xEwEJ4v7 b3fF1+EaT5AW+afBXIktFInno44pVQ==
anime.my. 7043 IN RRSIG NS 10 2 7200 20120830022534 20120809012534 18819 anime.my. K1FrXpvSybm29pwPZRYRmL+4yXtes695jM6zliVMFkYLQUik/k3jNShC RI+DbIVRoF0o2cbnQq94kzrjNOekdPkq/olNilExBcUlupzCEWE/lXVx XvZTMT8i3mAWnkNUZpSXWfTACoggc5rA5hRcESZzZFk3X14nUA/ZHlVK UUG2uRn8B2HP5JwP8GLO1wt3BMKFFyYU9Qw9I6EHOcQpnKDp5DdymPmV CKczMZoAkfqplEFNenvFwtonarB131OVkJhVIzMZ5Yf2ap4lFyO2KbO+ uwXprUdKJyARnPWQmVDUO9+Z4RnmzvQh5IxzVrt9zK/SrerTX1jBb35p TFbvDw==;; Query time: 4 msec
;; SERVER: 2001:4f8:3:2bc:1:0:64:21#53(2001:4f8:3:2bc:1:0:64:21)
;; WHEN: Sat Aug 11 20:14:05 2012
;; MSG SIZE rcvd: 1068
Miscellaneous:-
How to install BIND 9.9 on CentOS 5 32-bit?
- Install CentALT repo and EPEL (its dependency).
# rpm -Uvh http://centos.alt.ru/repository/centos/5/i386/centalt-release-5-3.noarch.rpm
# rpm -Uvh http://mirrors.buyvm.net/epel/5/i386/epel-release-5-4.noarch.rpm (if you are a BuyVM customer).
# rpm -Uvh http://download.fedoraproject.org/pub/epel/5/i386/epel-release-5-4.noarch.rpm (if you aren’t).
- Install BIND
# yum install bind
How to enable NSEC3?
In the shell, type:-
# rndc signing -nsec3param 1 0 10 <salt> <zone name>
salt: any phrase that contains the base 16 characters (0-F)
zone name: the DNSSEC-enabled zone you want to put the NSEC3 thingy into.
If you want to turn on opt-out option, change the middle number to 1.






















